Span Port vs. Network Tap
Posted 13 Oct at 12:00 pm in Productivity
Span Port vs. Network Tap
Span Port vs. Network Tap – which is best for you?
Network taps and span ports serve a similar purpose but operate in different ways. Network taps are usually passive, and create a copy of all traffic on a network link, while span ports are active devices that mirror traffic. The biggest difference is that a network tap will never drop a frame, span ports may. Today we’ll be discussing span ports vs. network taps.
Network Taps
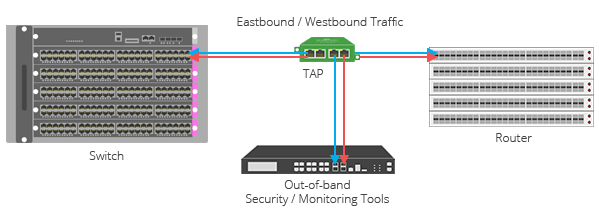
Network Test Access Points, or Network taps, are physical devices that are inserted into a network link. They make a duplicate of all traffic on a link, that is then sent to one or more monitoring devices. Again, network taps passive devices which means they do not interfere with the performance of the network.
Network taps are often used for security monitoring, intrusion detection/identification, and performance monitoring. They can also be used to troubleshoot network problems.
Advantages of Network Taps
- Passive: Network taps do not affect the performance of the network.
- Comprehensive: They capture all traffic from a network link.
- Scalable: They can monitor large networks regardless of the volume.
Disadvantages of Network Taps
- Cost: Can quickly become costly
- Installation: Installation can be difficult, especially for non-experienced individuals.
Span Ports
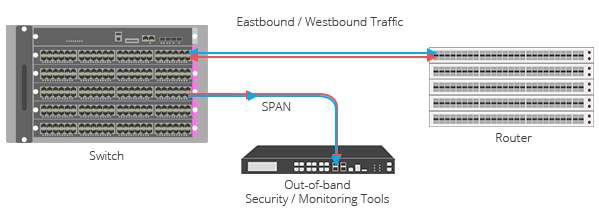
Span ports are switch features that mirror a piece of traffic from a network link to a monitoring device. Span ports are active, which also means they can be disruptive. They are, similar to network taps, used for performance monitoring, troubleshooting, and threat detection.
Advantages of Span Ports
- Ease of use: Easier to install and configure compared to a network tap.
- Cost: Can be much cheaper than a network tap.
Disadvantages of Span Ports
- Interference: They can affect network performance
- Limited: Span ports can only capture a smaller piece of traffic
- Scalability: Not as scalable which may not meet the needs of larger networks or higher traffic volumes.
So… Span Port vs. Network Tap, Which to Choose
At the end of the day, there is no “better option”, the best option is the one that makes the most sense for you. If you need to capture all of your traffic, a network tap is likely your better choice. If you only need to capture a smaller piece of traffic, and are less inclined to manage a possible headache of a set-up, you may want to side with a span port.
Some good general guidelines and things to remember:
- Security monitoring: Use a network tap if you need to capture all traffic on a network link for security monitoring purposes.
- Network performance monitoring: Use a span port if you only need to capture a subset of traffic for network performance monitoring purposes.
- Troubleshooting: Use a span port if you need to troubleshoot a network problem.
Example Scenarios
- Security monitoring: A large enterprise network with hundreds of servers and thousands of users needs to monitor all traffic on the network for security threats. The best solution would be to use a network tap to capture all traffic and send it to a security monitoring system.
- Network performance monitoring: A small business network with a few servers and a few dozen users needs to monitor network performance to ensure that applications are running smoothly. The best solution would be to use span ports to mirror a subset of traffic from each server to a network monitoring system.
- Troubleshooting: A network administrator is troubleshooting a network problem on a switch. The best solution would be to use a span port to mirror all traffic from the affected port to a laptop so that the administrator can analyze the traffic.
Conclusion
As we said before, there is no better option. Each option has its place and companies that it works best for. While they have their differences, they both serve a similar purpose. To ask Span port vs. network tap is perhaps the wrong approach to the problem – instead, think of your problems and which one fits those needs more precisely.
If you find this article to be useful, and would like to read more similar to this, check out our blog here.



No Comments